This is the most innovative technique of breaching security that I have come across. You will surprised to know about this new vulnerability. Recently, two security researchers, during the demonstration last week at the CanSecWest conference in Vancouver showed how hacking a PC’s BIOS is an easy job.
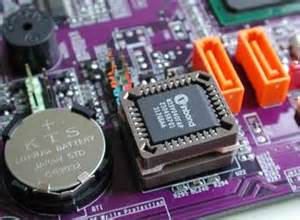
BIOS stands for Basic Input / Output System and is the first major software that loads on your computer system when it boots. It contains a set of rules or instructions that is needed in order to set up a communication between the operating system and the hardware.
Last week, the LegbaCore researchers showed how millions of computers contain vulnerabilities in their local BIOS chips, giving attackers a golden chance to perform malicious activities. Using this to their advantage, attackers can easily steal data and information from your system in a few minutes and can damage the system permanently.
SMM Incursion vulnerability in BIOS
While demonstrating the issue, researchers showed different vulnerabilities in SMM or System Management Mode. The role of the SMM mode of an Intel Processor is to allow the firmware to perform system functions. By gaining control of the SMM mode attackers can easily gain access to encrypted data including password as well.
Researchers Corey Kallenberg and Xeno Kovah explained how vulnerable the UEFI BIOS implementation carried out on the modern motherboards are. The US National Security Agency is more likely using the same techniques as suggested by these two researchers.
SMM malware gives attackers an ability to read all data that are present in the machine’s memory. Both researchers during the demo show how easily they were able to access the BIOS and then at the same time installed “Light Eater SMM payload”. “Light Eater SMM payload” is a malware that has the capability to extract GPG keys, passwords and steal decrypted messages from the Tails on an MSI computer where Tails is a privacy and security-oriented operating system.
How attackers can attack your system:
There are two ways which attackers can adopt to install the BIOS malware on your system. First one is through malware infection on your system either by an infected email or drive-by download and the second is when they physically get access to your computer.
How to prevent system from being attacked:
One of the best ways to protect your system and the data in it is by updating your BIOS to the latest version on the regular basis. Most of the people don’t install BIOS updates at all which give the attackers a chance to attack their system.
These LegbaCore Researchers have already reported several manufacturers about the issue who are now working towards a solution.
Thanks for reporting this, so more can take precautions. I’ve found on my Acer laptops sporting Windows 7 and dating to September 2010 manufacture, Acer not once (by auto or manual checks) ever had an update for BIOS (or anything else possible). So for the last two years I’ve had complex firewalling, requirement everything ask for internet permission first time every OS sesssion, of course active AV and file-level alteration protection, TrendMicro and other manual scanners that can check for kernel-level and “disk outside of OS” malware hooks, and as some modern malware can be so zipped/encrypted or wait until reboot to bypass AV…of course deletion of the pagefile each OS session end (to ensure nothing can “come alive” on next use).
So far, this works pretty well in combination with what’s also available with browser configs; Sality, other tdss, and newer trojans/zombies/lockers used to sneak past (showing infiltration of BIOS) until I “boiled the sea”…but that’s what you have to do when an OEM doesn’t update; it’s cheaper than buying new pc’s every few months, and you can do more harm than good on some models if you chance flashing the BIOS on your own with third-party stuff.
Again, you’re not joking about this matter, and thank for reporting more on it. Cheers!
I agree, updating the BIOS is easier said than done, and could lead to unwanted consequences for the layman.
Frightening, how does one update the BIOS
There are tools to update that Buck, however let me tell you BIOS changes should be done only in the presence of an expert or somebody with knowledge of the same.
OK thanks for that info Ankit
On another subject does anyone know why the same updates are received almost everyday one is Cumulative Security Update for Internet Explorer 11 for Windows 7 for x64-based Systems (KB3021952) I get this and similar ones with the same number almost everyday
Maybe this post ‘Windows Update repeatedly offers the same update’ will help:
http://forum.thewindowsclub.com/windows-tips-tutorials-articles/31446-fix-windows-update-repeatedly-offers-same-update.html
A little bit on this here: http://www.thewindowsclub.com/what-is-bios-in-computers-how-does-it-work
Thanks mate I’ll go there now
I unknowingly installed this on one of my computers and it rapidly spread to the other 8 computers, tablets and my mobile phones. I have yet to remove the dummy bios. Whoever has taken over my machines is recording me through video and audio and doing a whole bunch of printing…there is no reason for this since I AM NOBODY! I have to reinstall my OS at least three times a month. I traced the software to a software pirate site on Facebook…freeware sys and dilshad sys. Once the have your pc they can transfer files to your pc through facebook…I could go on and on…personally I believe its NSA…