Researchers have come across a new technique employed by hackers to drop a payload using an infected MS-Word document. Similar to a recent incident where hackers were caught fooling people into installing a Remote Access Tool (RAT) using a fake Norton LifeLock document, researchers at Sophos Labs have discovered a new Trickbot campaign targeting Italian e-mail addresses.
Playing on people’s fear of Coronavirus outbreak
Hackers are trying to play on people’s fear of the Coronavirus (COVID-19) outbreak in the country, which is equally serious to other campaigns with a similar modus operandi.
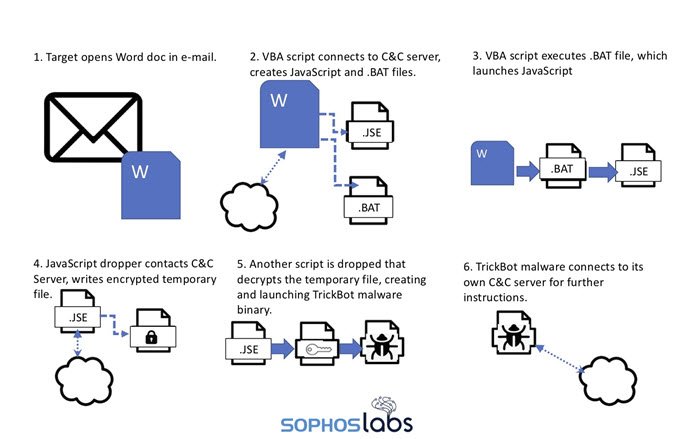
As always, it all starts with an e-mail that carries a malicious document. This document claims to provide a list of precautions to take to prevent Coronavirus (COVID-19) infection. The attached Word document comprises a Visual Basic for Applications (VBA) script as a macro. This script drops a payload that ultimately delivers a new Trickbot variant.
Although hackers playing on people’s fear of ‘Coronavirus’ may be new. However, the method to deliver the Trickbot malware with the help of the enclosed scripted Word document has been active for quite a few months now.
Previously, emails with subject lines such as “You have an email about your credit” and “You have received a fax about your loan” were highly common. Now, hackers seem to have turned their focus towards the Coronavirus scare.
“With concerns about COVID-19 on the rise – particularly in Italy, where cases are surging – the spam campaign’s subject line is now in tune with the concerns of the day.”
These emails carry a message recommending readers to open the enclosed document.
If Macros are disabled, the Word document opens with a message asking the recipient to enable editing and content because “this document was created in an earlier version of Microsoft Office Word.” But if macros are already enabled, it calls the macro file.
The process ultimately infects your system with Trickbot malware. In a nutshell, it’s a banking trojan that targets sensitive information and serves as a dropper for other malware.
Researchers recommend users to disable macros in Office applications for all but the most trusted documents. Users should also refrain from opening documents received via untrustworthy emails.
Leave a Reply