Over the last few days, we have come across several security and privacy issues with the video conferencing service: Zoom, a popular enterprise video-conferencing service that allows users to host online meetings and connect with colleagues remotely.
Security researchers at TrendMicro have come across a Coinminer malware bundled with the official installer of the Zoom video conferencing app, trying to trick users into downloading a malicious file onto the client machine.
Coinminer is being bundled with Zoom installer
However, the compromised files are not from Zoom’s official download center. Researchers believe those compromised files might have originated from fraudulent websites.
Most of the companies worldwide have transitioned to work-from-home arrangements in the wake of the ongoing coronavirus COVID-19 outbreak.
As a result, the consumption of Zoom has skyrocketed like never before. That’s probably also why hackers are trying to take advantage of the ongoing disruptions to spread malware.
“Zoom as a brand is being abused right now, more than it ever has been,” said John Shier, Senior Security Expert at Sophos Labs, when he spoke exclusively to me:
“In this sense, there are two victims. The victims who receive the spam might act on it, click on the link, either fill in their [login] details or download a piece of malware. Zoom themselves are victims as well because their brand is being abused to send out and lend legitimacy to a lot of these phishers.”
Upon analyzing the installer, Trend Micro researchers have discovered that users trying to download the installer end up downloading additional files including the AutoIt compiled malware Trojan.Win32.MOOZ.THCCABO.
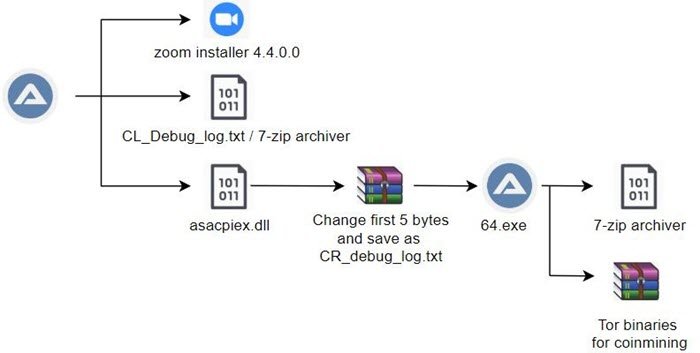
Following is the list of file it drops alongside the legitimate Zoom installer:
- 64.exe
- asacpiex.dll (first 5 bytes are NULL)
- CR_Debug_Log.txt (asacpiex.dll with the first 5 bytes replaced)
- CL_Debug_Log.txt
- SystemCheck.xml
- ZoomInstaller.exe
Researchers demonstrate that the archive file asascpiex.dll makes it difficult to determine its original file signature. The file is then copied as CR_Debug_log.txt. 7-Zip archiver CL_Debug_log.txt is used to decompress the password-protected archive.
Furthermore, it determines the system architecture using the cpuinfo flags bits. It will drop 64.exe for 64-bit systems. Interestingly, the malware only runs in a 64-bit environment.
It collects information such as Graphics Processing Unit (GPU) information using Windows Management Instrumentation (WMI queries). It also collects information on CPU, system, operating system version, video controllers, and processors.
It examines whether the Microsoft SmartScreen and Windows Defender are enabled and if the system is running antivirus software. It sends the collected data to hxxps://2no.co/1IRnc using HTTP GET request.
Meanwhile, the CR_Debug_log.txt file contains the payload 64.exe coinminer and installs an AutoIt compiled malware. It also can also evade detection.
Stay safe and make sure to download the installer from the official Zoom website to avoid such compromise.
Leave a Reply